I recently blogged about the Inoculation technique as an effective deterrent for many malicious threats. It seems the bad guys understand this as well, and are using it as a competitive advantage. You see malware isn’t just a threat to your personal data, it’s also a threat to other malware authors that are fighting for that same data.
This threat goes by many ambiguous names; Gen:Variant.Jaik.3565, Backdoor/Win32.Zegost, Trojan:Win32/ServStart.gen!A, Win32:Trojan-gen, Trojan.Win32.Swizzor.c, Obfuscated_O, but unfortunately a lot of unrelated malware is also detect by many of these same names so I just call it YourLife [the code contains the string ‘byfl’ which sometimes stands for ‘Battle For Your Life’, seems fitting as this threat is battling for your digital life].
When run, the YourLife trojan installs itself as the “Microsoft Software ks8” service, a play on Microsoft and Kaspersky Security 8.0.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\ks8
“Description” = Thank you for use ks8
“DisplayName” = Microsoft Software ks8
“ErrorControl” = 0
“ImagePath” = C:\Windows\system32\<varies>.exe
“ObjectName” = LocalSystem
“Start” = 2
“Type” = 10
The malware is copied to %WinDir%\system32\<varies>.exe and %WinDir%\vmtoolsd.exe. vmtoolsd.exe is the name of a legitimate program from VMWare that is commonly found on malware analysis systems and a trigger for many malicious threats to skip infection routines in the hope of flying under the radar to evade being discovered. In this case, YourLife is banking on the name vmtoolsd.exe assisting in its self-preservation, to keep the infected host all to itself. Another trick up its sleeve is for the main service to monitor the vmtoolsd.exe process and restart it should the process be terminated.
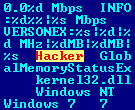
Beyond this, the trojan attempts to relay system information to a remote server, including:
- Hardware specs (CPU, RAM, etc)
- OS version
- Bandwidth speed
Typical data points for a botnet.
About half of the major Antivirus signatures detect this threat at the time of this writing.