Summary
Trick malware into intentionally not infecting your machine by making it appear as a malware hunting system. Simpy follow these few steps below.
Details
The best defense against malicious software is a layered defense. This includes the use of various technologies:
- Access Control
- Anti-virus
- Email filtering (anti-spam)
- Host Intrusion Prevention
- Network Intrusion Prevention
- Web filtering (domain, IP, and URL filtering)
Most consumer anti-malware suites include a combination of these techniques, but there is another that is virtually, if not completely, absent. That is what I’ll call inoculation. This approach uses the attackers’ tactics against them. You see malware authors know their creations can have a longer lifespan if they can make it harder for researchers to reverse engineer. Just as, if not more important, is their ability to conceal malicious actions during automated analysis. In both of these cases, the use of virtual machines (VMs) greatly assist the good guys in threat analysis, countermeasure creation, and testing. So if the malware is “VM-aware” it can simply exit or crash without carrying out the intended nefarious mission, allowing that threat to live another day.
While VM-aware threats can be a nuisance for researchers, it can also be a blessing for would-be victims. There are a number of methods that can be used to determine whether the system is physical or virtual, and some are more complex than others. Most vm-aware threats stick to the basics, which is good for us. To thwart these programs, dummy (or decoy) files, registry entries, and processes, can be created to fool the offending software.
Now this in no means replaces the aforementioned security suite defenses, it’s merely supplemental. And it is also only effective on a portion of malware. However, these changes take up tiny fraction of system resources and have virtually no negative performance impact. So there’s very little reason not to inoculate yourself. If there is any downside, it’s the potential for non-malicious programs to also bail out in the presence of virtualized environment. They might due this to evade reverse engineering or cracking (such as people trying to convert trial versions to paid ones).
I’ll update this post with different inoculations, but here’s one for starters.
VMWare tools detection inoculation
VMWare is one of the most popular VMs. It runs a set of tool programs inside the guest that allow for interacting with the host for various functions, such as copy/paste, drag/drop, etc. There are many ways to detect VMWare tools are present, but a common basic way is to check for the running process named “vmtoolsd.exe”. This snippet below copies a very small standard windows program to the Start Up folder with that name and executes it. This ensures that each time the system is started, the decoy process is running.
- Copy the following text:
cmd /c copy %windir%\system32\plasrv.exe "%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\vmtoolsd.exe" & "%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\vmtoolsd.exe"
- Hit the WINDOWS key on the keyboard and R at the same time (WINDOWS + R), and PASTE into the Open field.
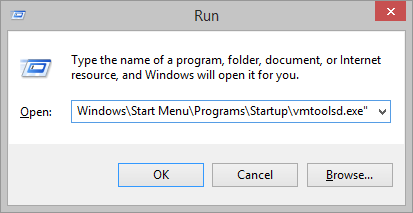
- Hit ENTER. The following Window should appear confirming that this worked:
- That’s it! But if you want to further confirm that it worked, you can run Task Manager (Click the START BUTTON, type TASKMGR, and hit ENTER). Under the PROCESSES tab you should see “vmtoolsd.exe” (along with many other processes):
Windows 8 Windows 7
Pingback: Recent “Our Photo” Spam Run | Getvirushelp
Pingback: Territorial Malware, YourLife, Uses Innoculation Tactic to Keep Others Off Turf | Getvirushelp